- Operation without any prior knowledge about the protected system
- Combination of the fast signature-based analysis for known protocols and versatile parsing algorithms for unknown protocols
- All operations are based on the copy of the network traffic received from the assets
- Comprehensive system modeling
- Reliable anomaly detection;
-
Machine learning technologies for early anomaly detection
-
Assets and network interactions inventory
-
Behavioral analysis of the protected system and its components
-
Automated system modeling
CL Thymus modeling algorithm analyzes the data obtained from passive ICS operation observation and does not require bidirectional communication with the assets.
The basis of CL Thymus is a patented anomaly detection method. This method comprises two modules:
- Unknown traffic analysis and deep packet inspection module
- Multiagent modeling module
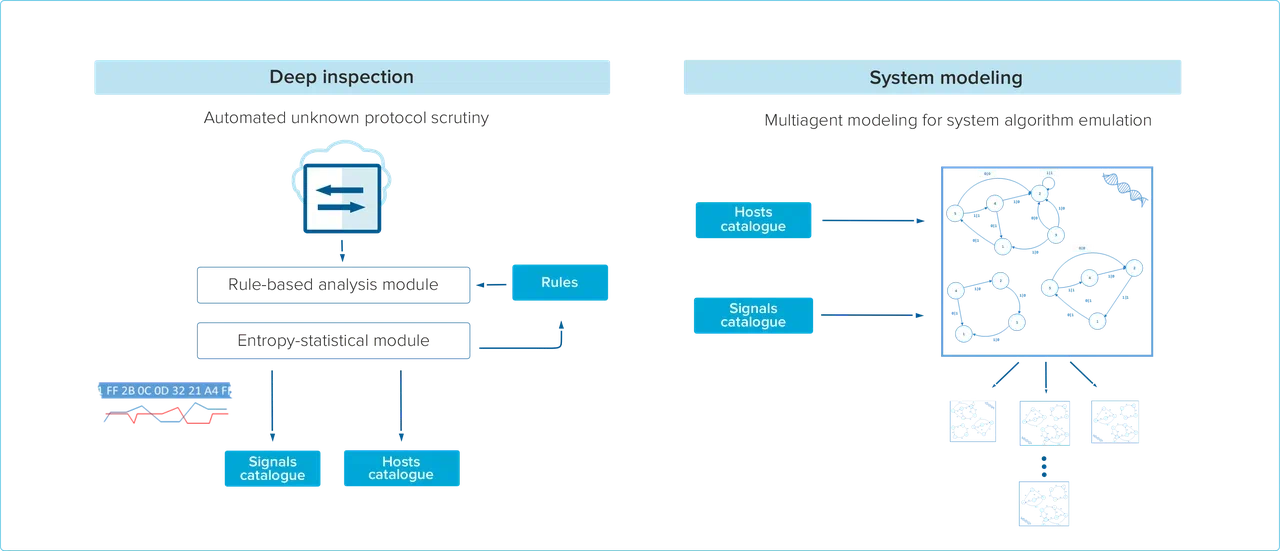
Basic traffic analysis module extracts information from collected network packets using deep packet inspection. All discovered unknown traffic is stored for further analysis. For each unparsed packet several parameters including entropy, mutual information and perplexity are calculated. The results of the process allow CL Thymus to define protocol structure and semantics, detect fields and their content and ultimately build the network connectivity model for the protected assets
The multiagent approach considers each asset or service of the protected system as an agent, therefore the whole system can be represented by a set of agents interacting with each other. Multiagent modeling approach helps both anomaly detection and identification operations
- Unknown network traffic is parsed and rules for subsequent analysis are generated
- Network topology and addressing scheme are defined
- Assets, network nodes and services are determined and modeled
Training can be performed using one or several model training methods until the model reaches desired forecast accuracy methods.
After the model has been trained, the following events are considered anomalies in the system operation
- Modifications to the address hierarchy
- New nodes on the network
- New network services for existing nodes
- Other network-related changes
- Differences between actual observed output signals and predicted output signals based on the system model and observed input signals
CL Thymus engine allows for accurate anomaly localization down to the simulated system component, determining all input signals and conditions that may have impacted normal asset operation.
The model can be further fine-tuned by accounting for the false positives detected by CL Thymus.



